Space Odyssey
An Experimental Security Analysis of Satellites
Johannes Willbold*,
Moritz Schloegel*‡, Manuel Vögele*, Maximilian Gerhardt*,
Thorsten Holz‡, Ali Abbasi‡
*
‡
v1.3
Distinguished Paper
Applications
Context
Motivation
?
?
Approach
Firmware Analysis
Attack Goals
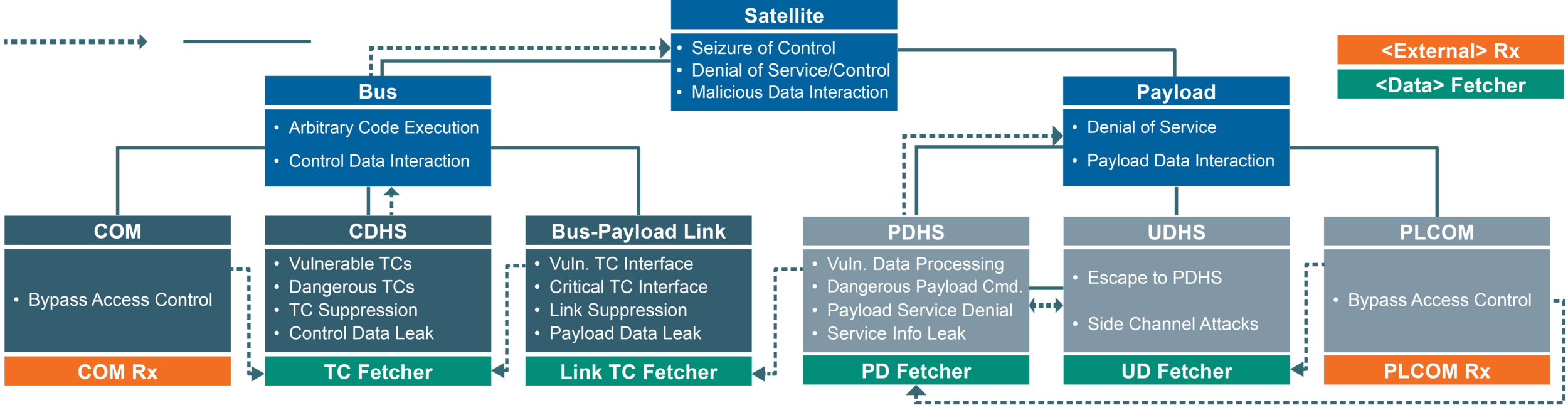
Bus / Payload
Bus
Bus / Payload
Threats
Threats
Arb. Code Execution Control Data Interaction
Threats
Arb. Code Execution Control Data Interaction
Denial of Service Payload Data Interaction
Threats
- Arb. Code Execution
- Control Data Interaction
Denial of Service Payload Data Interaction
- Vulnerable TC
- Dangerous TC
- [ ... ]
- [ ... ]
Bypass Access Control
[...]
[...]
Threats
Arb. Code Execution Control Data Interaction
Denial of Service Payload Data Interaction
- Vulnerable TC
- Dangerous TC
- [ ... ]
- [ ... ]
Bypass Access Control
[...]
[...]
Bus-Payload Link
Threats
Vulnerable TC Dangerous TC TC Suppression Control Data Leak
Arb. Code Execution Control Data Interaction
Denial of Service Payload Data Interaction
Bus-Payload Link
COM Rx
PLCOM Rx
PD Fetcher
TC Fetcher
Bypass Access Control
[...]
[...]
More Threats
OPS-Sat
1
2
3
European Space Agency (ESA) Satellite
Actively Operated
Launched 2019
OPS-Sat
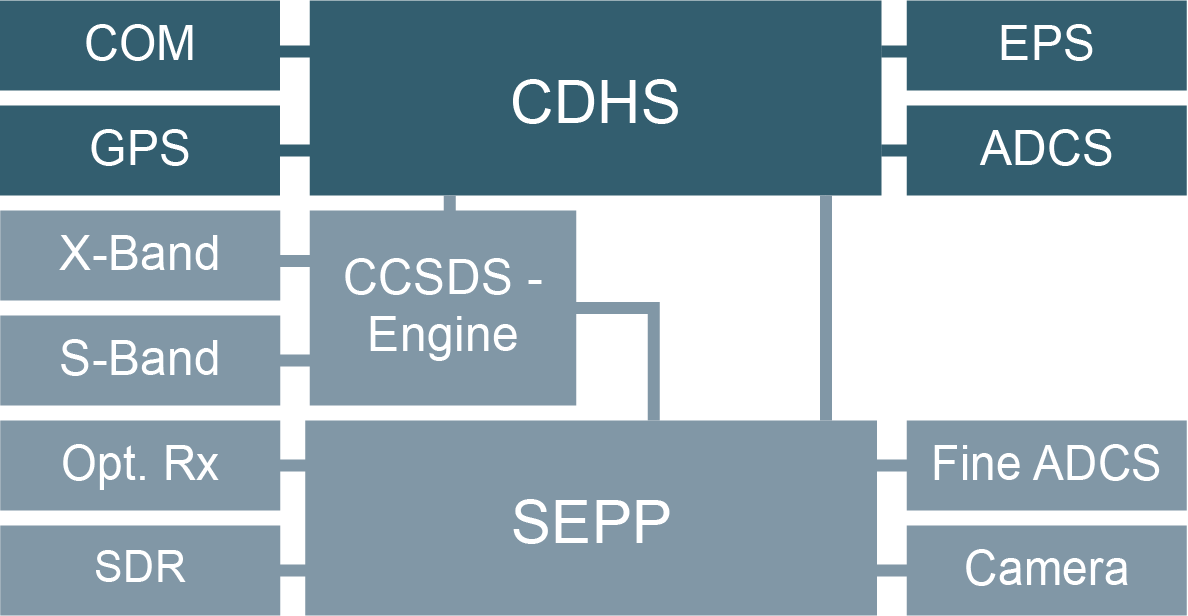
Bus
Payload
OPS-Sat

Payload
COM
S-Band COM
Bus-Pl. Link
COM
PDHS
All Potential Attack Path
Our Attack Paths
OPS-Sat
- Bypass Access Control
- Missing Access Control
- Vulnerable TC
- Stack Buffer Overflow
- Arbitrary Code Execution
- Missing OS Defenses
Mission accomplished: Control seized
Survey
Space Agencies
Universities
Companies
Fully Anonymous
10 x 1-50 kg
2 x 50-100 kg
5 x > 100 kg
TC Protection
Question: Are any measures deployed to prevent 3rd parties from controlling your satellite?
Unknown*:
Prefer not to say / Don't know
2
4
6
8
9
3
5
Yes
No
Unknown*
TC Obscurity
Question: What measures are deployed to prevent 3rd parties from controlling your satellite? (Multiple Answers)
2
4
4
5
Access Control
Encryption
3
*: Special knowledge about ....
Special permit needed
* ... Frequences, Modulation, etc.
* ... Protocols
3
2
Satellite Threat Taxonomy
Security Analysis of 3 Satellites
Survey amongst Professionals
Conclusion
- Satellite Threat Taxonomy
- External Attacker → COM → CDHS → Seizure of Control
- Security Analysis of 3 Satellites
- Successful exploitation of several vulnerabilities
- Missing state-of-the-art defenses
- Survey amongst professionals
- Supports our results
- Security-by-obscurity prevails