Space Invaders
An Experimental Security Analysis of LEO Satellites
Johannes Willbold
@jwillbold
/jwillbold
jwillbold
Slides
Get it while its hot!
Mission Briefing
Objective
Target
Intel
Finale
Finale
Hostile Takeover & Lockout
ESA's OPS-Sat
ESA's OPS-Sat
ESA's OPS-Sat
ESA's OPS-Sat
$whoami

- Satellite & Space Systems Security
- PhD Student
- Ruhr University Bochum, DE
- Co-Founder of SpaceSec
- Visiting Researcher
- Cyber-Defence Campus, CH
- 2022 CySat Speaker
Space Odyssey

44th IEEE Symposium on Security and Privacy (S&P)
Our Journey ...
Firmware Attacks
Security Analysis
Live Demo
Lessons Learnt
Firmware Attacks
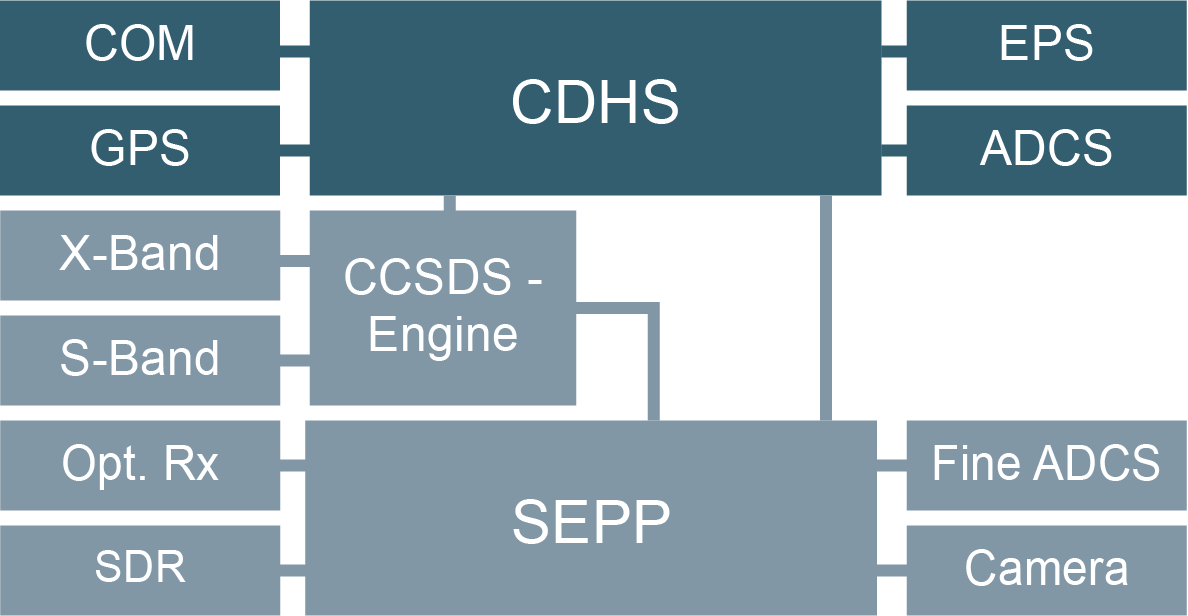
Components
COM
Payload
CDHS
EPS
ADCS
Components
Payload
PLCOM
COM
CDHS
Bus
Components
Payload
PLCOM
- Hack CySat 2022
-
How I hacked an ESA's experimental satellite
- Maurice-Michel Didelot
- Tomorrow
- Matteo Calabrese
- Hack CySat 2023
COM
CDHS
Bus
Components
- Bypass COM Protection
- Missing AC
- Insecure Protocol
- Outdated Crypto
- Timing Side Channels
- Leaked Keys
- Timed Backdoor
- ...
COM
CDHS
Bus
Components
- Bypass COM Protection
- [...]
COM
CDHS
- Deploy Attacker Payload
- Firmware Update
- Signed Image
- Slow Upload
- Comples System
- Firmware Update
Bus
Components
- Bypass COM Protection
- [...]
COM
CDHS
Bus
- Deploy Attacker Payload
Firmware Update- Dangerous TC
- Vulnerbale TC
- Hijack Bus Control Flow
- Full Bus Privileges
Objectives
1
2
3
4
Bypass COM Protection
Dangerous / Vulnerable TC
Hijack Bus Control Flow
Full Bus Privileges
Security Analysis


Awesome Sat
OPS-Sat
Peripherals
S-/X-Band, SDR, Optical Rx., Camera, ...
Launched
December 2019
Payload Plattform
ARM-Based Linux + FPGA
Operated by ESA
Open for Research
System Chart
- Bypass COM Protection
- Dangerous / Vulnerable TC
-
memcpy as TC
- Config Changes
- Quick/Hot Patching
- Debugging
int sch_handler_set_raw_memory(scheduler_cmd_t* pCmd) {
raw_mem_access_cmd_t* pAddr = pCmd−>pCmdArgs;
char* pWriteData;
if (pAddr) {
if (g_sch_exec_mode != 1 ) {
/* exception and return */
}
char* pWriteData = &pAddr−>start_of_data_buf;
if (pAddr−>filesystem_target) {
// [...]
} else {
memcpy(pAddr−>targetAddr,
&pAddr−>start_of_data_buf,
pAddr−>writeLength);
}
}
// ...
}System Chart

System Chart

Message Abstraction Layer (MAL)
S-Band
Space Packet Protocol (SPP)
PUBSUB_MonitorEvent
SUBMIT_SetPowerState
INVOKE_GetGPSData
...
PROGRESS_GetSummary
Custom Byte Parsing
ADCS Server
...
UHF
Cubesat Space Protocol (CSP)
Parameter DB
CSP => SPP
void task_adcs_servr() {
char log_file_name [32];
csp_listen(socket, 10);
csp_bind(socket, port);
do {
do {
conn = csp_accept(socket, 0xff);
} while (do_wait_for_conn);
packet = csp_read(conn, 10);
if (packet) {
packet_data = packet->data;
switch(*packet_data) {
// [...]
case SET_LOGFILE: {
packet_data = packet->data + 0xf;
log_file_name[0] = '\0';
strcat(log_file_name,packet_data);
// ...
}
}
}
}
}
System Chart
ADCS Server
Cubesat Space Protocol (CSP)

- Bypass COM Protection
- Dangerous / Vulnerable TC
- Hijack Bus Control Flow
- No OS-Defenses
- ASLR
- NX Stack
- No SW-Defenses
- Stack Cookies
- No OS-Defenses

System Chart
- Bypass COM Protection
- Dangerous / Vulnerable TC
- Hijack Bus Control Flow
- Full Bus Privileges
- Privilege-free RTOS

System Chart
Demo Setup

Emulation Overview
QEMU
AVR32
OBSW
Simulation Agent
Sensors
UHF
TC Handlers
Telecommand
Telemtry
TCP
TCP
Flight Manuvers
Sensor Values
Live Demo
$> ./access-satellite.
[*] Uploading TC ...
[*] Deploying payload ...
[*] Payload written to flash ...
[*] Rebooting ...
[*] $$$Lessons Learnt
Firmware Attacks on Satellite are a thing
Just TC Execution is not Enough
Missing State-of-the-Art Defense
90s-style Buffer Overflows in Space Systems

Thanks!
- Firmware Attacks on Satellite
- External Attacker → COM → CDHS → $$$
- Satellite Exploitation Objectives
- Vulnerable & Dangerous TCs
- Missing OS & SW-Defenses
Johannes Willbold - johannes.willbold@rub.de
@jwillbold
/jwillbold
@jwillbold
Also visit my Talk @ REcon, Montreal, Canada
[Attribution] Icons: Font Awesome 5 Solid by Dave Gandy under CC BY 4.0
Colored Satellite: Space icons created by Freepik - Flaticon